|
|
@@ -0,0 +1,688 @@
|
|
|
+%!TEX program = xelatex
|
|
|
+\documentclass{beamer}
|
|
|
+
|
|
|
+\usepackage[english]{babel}
|
|
|
+
|
|
|
+\usepackage{graphicx,hyperref,url, materialbeamer}
|
|
|
+\usepackage{braket}
|
|
|
+%\usepackage{euler}
|
|
|
+\usepackage{listings}
|
|
|
+\usepackage{url}
|
|
|
+
|
|
|
+\usepackage{fontspec}
|
|
|
+\setmainfont{Roboto}
|
|
|
+
|
|
|
+\graphicspath{ {./img/} }
|
|
|
+\setbeamercovered{transparent}
|
|
|
+\lstdefinestyle{customsql}{
|
|
|
+ belowcaptionskip=1\baselineskip,
|
|
|
+ breaklines=true,
|
|
|
+ xleftmargin=\parindent,
|
|
|
+ language=SQL,
|
|
|
+ showstringspaces=false,
|
|
|
+ basicstyle=\footnotesize\ttfamily,
|
|
|
+ keywordstyle=\bfseries\color{green!40!black},
|
|
|
+ commentstyle=\itshape\color{purple!40!black},
|
|
|
+ identifierstyle=\color{blue},
|
|
|
+ stringstyle=\color{orange},
|
|
|
+}
|
|
|
+\lstset{escapechar=@,style=customsql}
|
|
|
+
|
|
|
+\usefonttheme{professionalfonts} % using non standard fonts for beamer
|
|
|
+%\usefonttheme{serif}
|
|
|
+
|
|
|
+% The title of the presentation:
|
|
|
+% - first a short version which is visible at the bottom of each slide;
|
|
|
+% - second the full title shown on the title slide;
|
|
|
+\title[CyberSec Trends 2018]{2018 Cyber\\ Security Trends}
|
|
|
+
|
|
|
+% Optional: a subtitle to be dispalyed on the title slide
|
|
|
+\subtitle{The Latest and the Greatest Changes to the Computer and Networks Security Paradigm}
|
|
|
+
|
|
|
+% The author(s) of the presentation:
|
|
|
+% - again first a short version to be displayed at the bottom;
|
|
|
+% - next the full list of authors, which may include contact information;
|
|
|
+\author[Prof. Sukumar Nandi]{
|
|
|
+ Prof. Sukumar Nandi}
|
|
|
+
|
|
|
+%\titlegraphic{\includegraphics[width=\textwidth]{atac-logo}}
|
|
|
+
|
|
|
+% The institute:
|
|
|
+% - to start the name of the university as displayed on the top of each slide
|
|
|
+% this can be adjusted such that you can also create a Dutch version
|
|
|
+% - next the institute information as displayed on the title slide
|
|
|
+\institute[Indian Institute of Technology Guwahati]{
|
|
|
+Department of Computer Science and Engineering\\
|
|
|
+ Indian Institute of Technology Guwahati \\
|
|
|
+ Email: sukumar@iitg.ernet.in}
|
|
|
+
|
|
|
+% Add a date and possibly the name of the event to the slides
|
|
|
+% - again first a short version to be shown at the bottom of each slide
|
|
|
+% - second the full date and event name for the title slide
|
|
|
+\date[\today]{
|
|
|
+ \today}
|
|
|
+
|
|
|
+
|
|
|
+
|
|
|
+
|
|
|
+\providecommand{\di}{\mathop{}\!\mathrm{d}}
|
|
|
+\providecommand*{\der}[3][]{\frac{d\if?#1?\else^{#1}\fi#2}{d #3\if?#1?\else^{#1}\fi}}
|
|
|
+ \providecommand*{\pder}[3][]{%
|
|
|
+ \frac{\partial\if?#1?\else^{#1}\fi#2}{\partial #3\if?#1?\else^{#1}\fi}%
|
|
|
+ }
|
|
|
+
|
|
|
+\setbeamertemplate{bibliography item}[text]
|
|
|
+\begin{document}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+ \titlepage
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+ \frametitle{Table of Contents}
|
|
|
+
|
|
|
+ \tableofcontents
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+%\input{introduction}
|
|
|
+%\input{datamodel}
|
|
|
+%\input{architechture}
|
|
|
+%\input{implementation}
|
|
|
+%\input{consistency}
|
|
|
+%\input{workload}
|
|
|
+
|
|
|
+\setlength{\parskip}{\baselineskip}
|
|
|
+\section{Introduction}
|
|
|
+\begin{frame}[t]
|
|
|
+\frametitle{Introduction}
|
|
|
+\begin{block}{Why do we need to stay up-to-date with cyber-security trends?}
|
|
|
+ \begin{itemize}
|
|
|
+ {\footnotesize \item Cyber-attacks evolve: ransomware are MITM are very common today.
|
|
|
+ \item Numerous exploits are found every minute.
|
|
|
+ \item Discovered exploits are also fixed over time.
|
|
|
+ \item New paradigms like IoT, smart home, vehicular networks, etc. increase attack surface.
|
|
|
+ \item We need to build secure systems to minimize cyber attacks.
|
|
|
+ \item We need to counter censorship and cyber-espionage by oppressive nation states.}
|
|
|
+ \end{itemize}
|
|
|
+\end{block}
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\section{System Security}
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Attacks on System Software}
|
|
|
+
|
|
|
+System software like firmware, bootloader, operating system and system utilities can be attacked in numerous ways.
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Malware due to running untrusted code: viruses, spyware, trojan horses, worms, ransomware etc.
|
|
|
+ \item Operating system, bootloader and firmware exploits.
|
|
|
+ \item Backdoors in applications, OS, bootloader and firmware.
|
|
|
+ \item Insufficient or poor OS security models.
|
|
|
+ \item Poor end-user awareness.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
+Malware are softwares which are specifically designed to disrupt, damage, or gain authorized access to a computer system.
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Malware usually infect the system either automatically by exploits or due to end-user action caused by poor judgement.
|
|
|
+ \item Antivirus and malware suites are no longer effective against these. In fact there are known cases, where increase the number of security holes \cite{anthony_2017,mahal_2016}. On Windows, the default Defender is sufficient.
|
|
|
+ \item Malware also affect non-PC and non-server platforms such as mobile devices and IoT devices like phones (RedDrop, Pegasus) and webcams (Mirai).
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
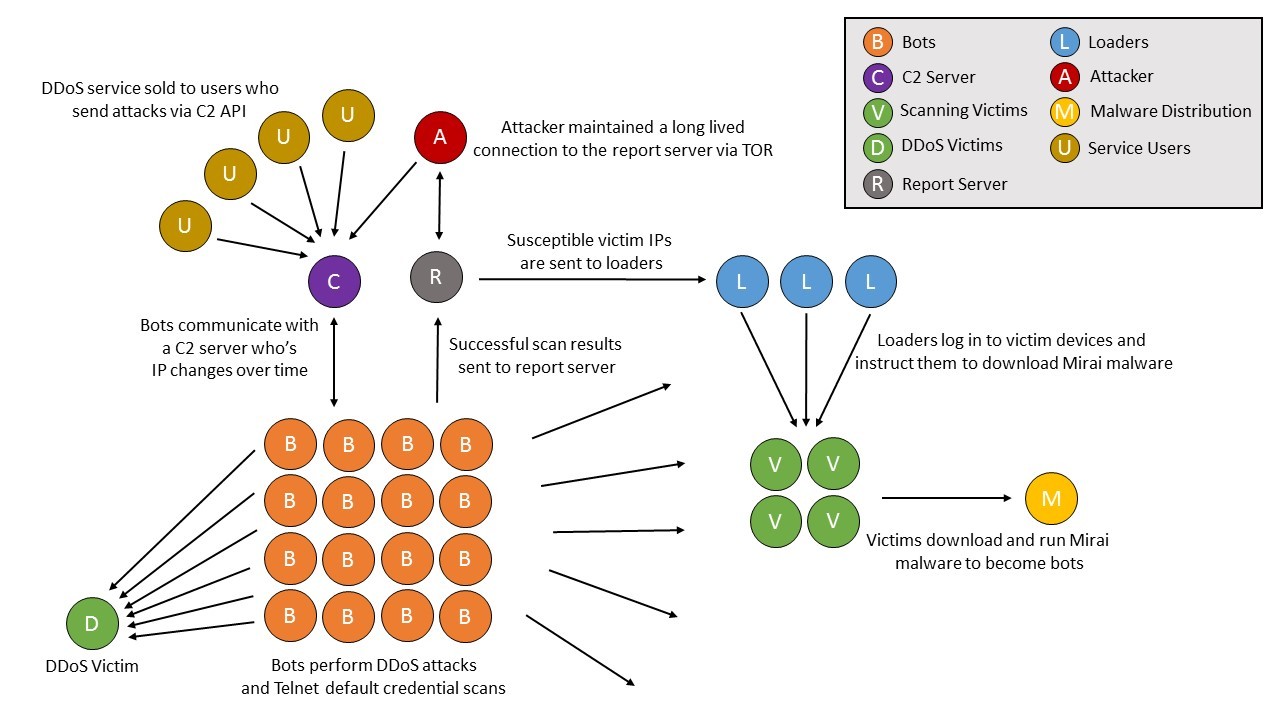
+\begin{block}{Mirai malware botnet structure}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=0.9\textwidth]{mirai.jpg}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
+Malware can be mitigated by following the given steps:
|
|
|
+\begin{itemize}
|
|
|
+ \item Updating OS, applications and firmware regularly.
|
|
|
+ \item If a product no longer receives software updates, limit usage and people accessing it to the bare minimum.
|
|
|
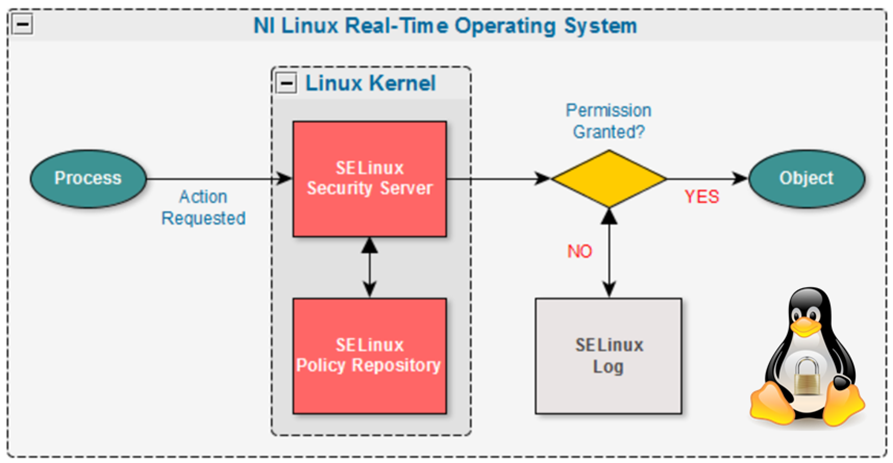
+ \item Using kernel level security measures like SELinux, AppArmor, grsecurity, OpenBSM, etc.
|
|
|
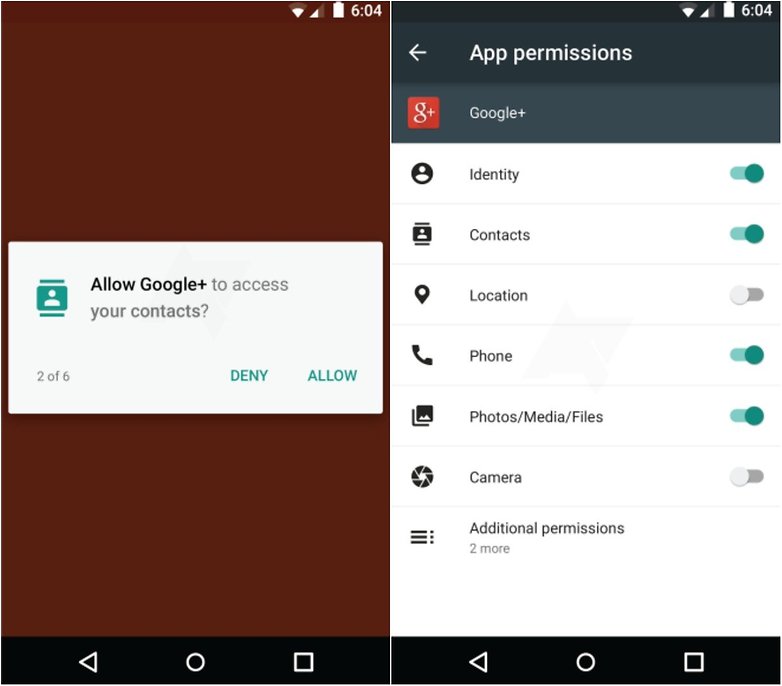
+ \item Avoid installing apps from unknown and untrusted sources.
|
|
|
+ \item Observing the permissions requested by an app before installing.
|
|
|
+ \item If using an untrusted app is needed, run it on a virtual machine (KVM, VMWare) or a container (Docker, LXC, BSD jails) to isolate it.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
+\begin{block}{SELinux workflow\cite{selinux}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=0.9\textwidth]{selinux.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
+\begin{block}{Android permissions\cite{androidpit}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[height=0.6\textheight]{android-permissions.jpg}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Malware}
|
|
|
+
|
|
|
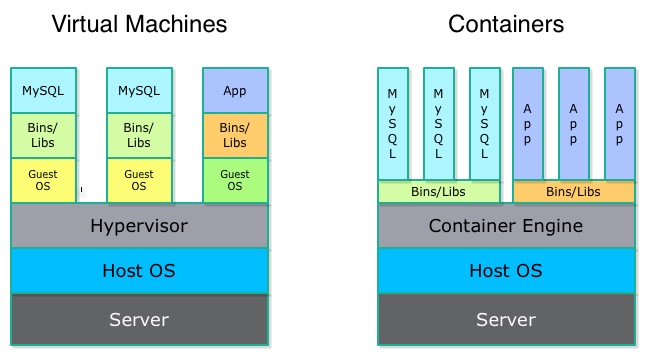
+\begin{block}{Virtual Machines and Containers\cite{cobb_2016}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=0.9\textwidth]{vms-and-cts.jpg}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Exploits}
|
|
|
+
|
|
|
+An exploit is a vulnerability in a computer system which allows an attacker to reduce its information assurance, security, control and performance.
|
|
|
+
|
|
|
+Exploits arise due to:
|
|
|
+{\footnotesize \begin{itemize}
|
|
|
+ \item Complexity of software code that leaves unintended access points.
|
|
|
+ \item Familiarity and reuse of software that allows an attacker to make an intelligent guess.
|
|
|
+ \item Fundamental operating system design flaws that grants full system access to a program.
|
|
|
+ \item Bugs left by the programmer in a software application.
|
|
|
+ \item Not sanitizing/validating user input and mishandling buffer overflow cases.
|
|
|
+ \item Not learning from past mistakes.
|
|
|
+\end{itemize}}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
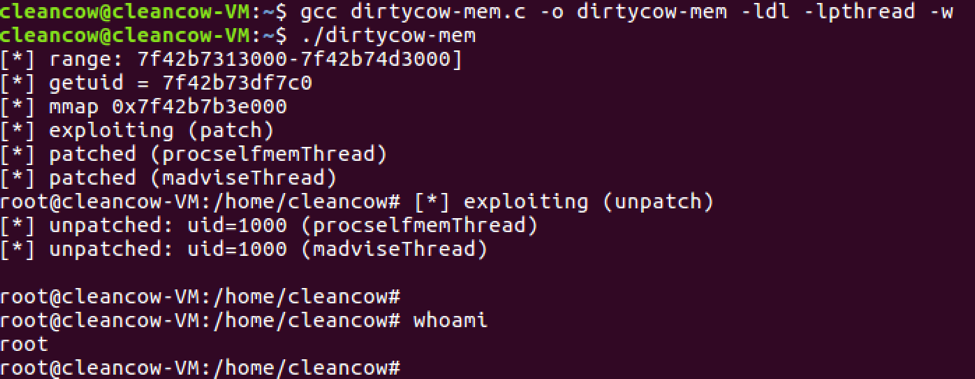
+\frametitle{Exploits}
|
|
|
+
|
|
|
+\begin{block}{Dirtycow local root exploit\cite{flashpoint_2016}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=\textwidth]{dirtycow.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Exploits}
|
|
|
+
|
|
|
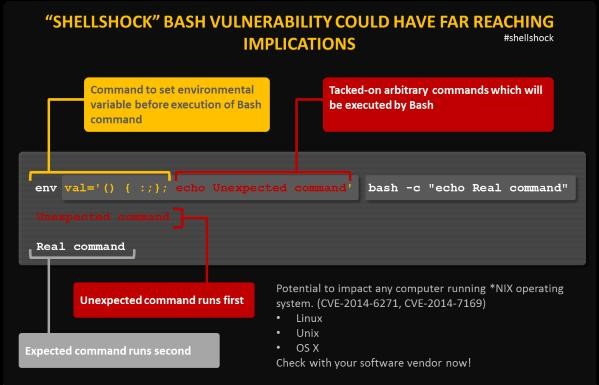
+\begin{block}{BASH Shellshock exploit\cite{infosec_resources_2015}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=0.9\textwidth]{shellshock.jpg}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Exploits}
|
|
|
+
|
|
|
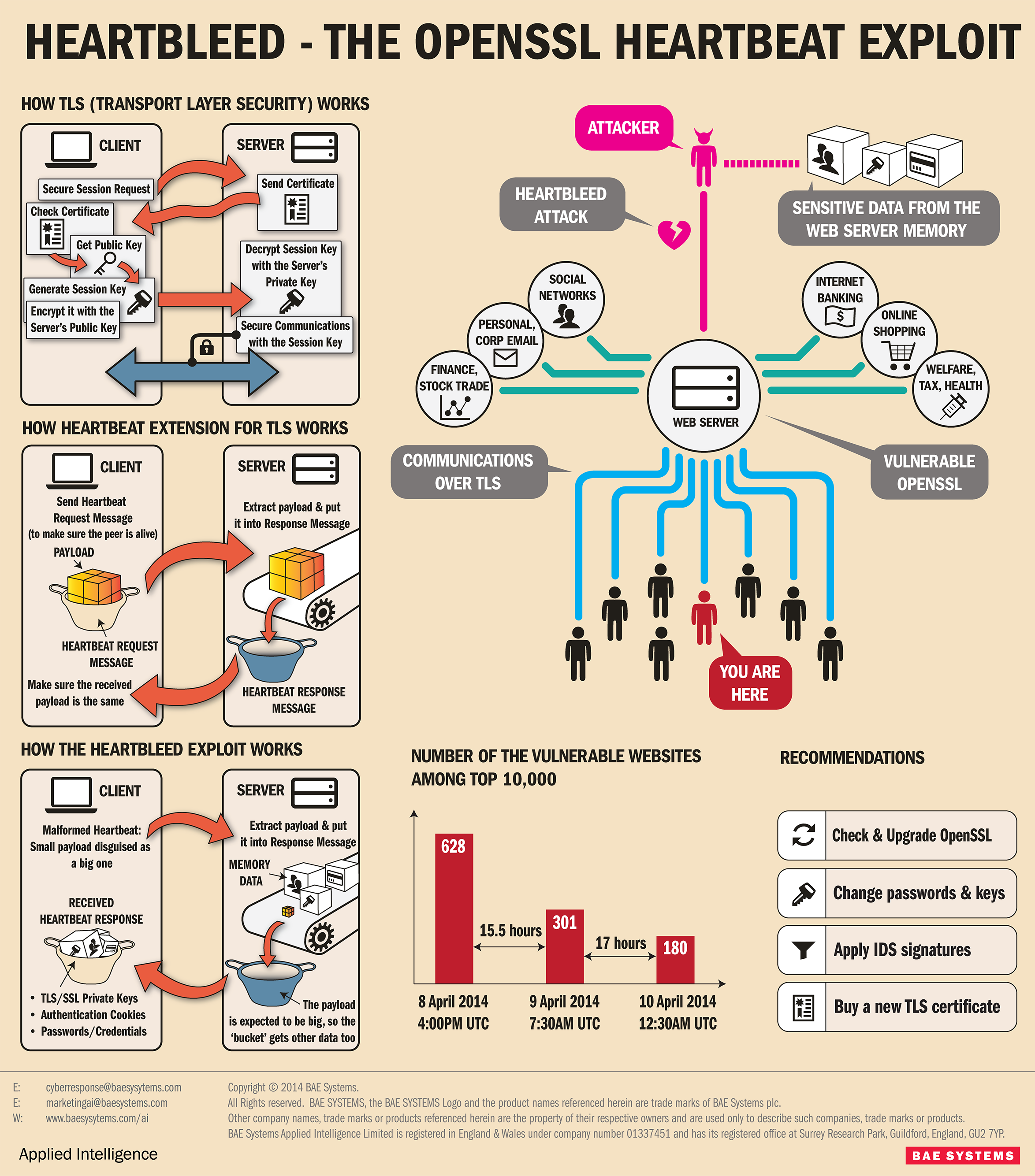
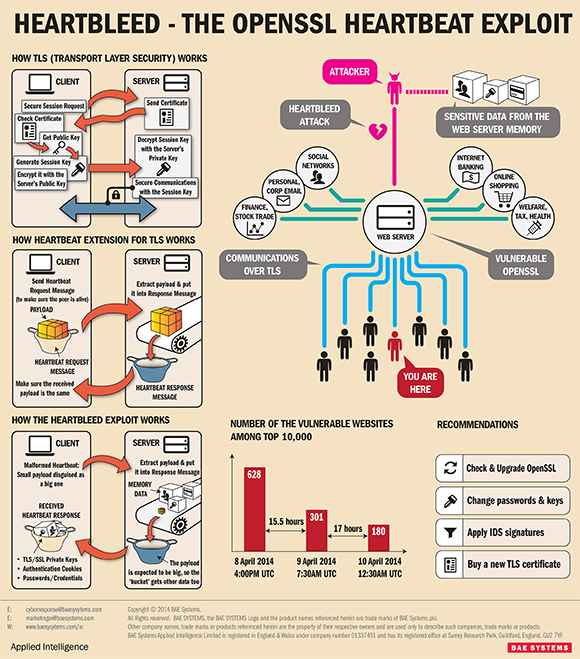
+\begin{block}{OpenSSL Heartbleed exploit\cite{searchsecurity}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[height=0.7\textheight]{heartbleed_2.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+%http://imgs.xkcd.com/comics/meltdown_and_spectre.png
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Exploits}
|
|
|
+
|
|
|
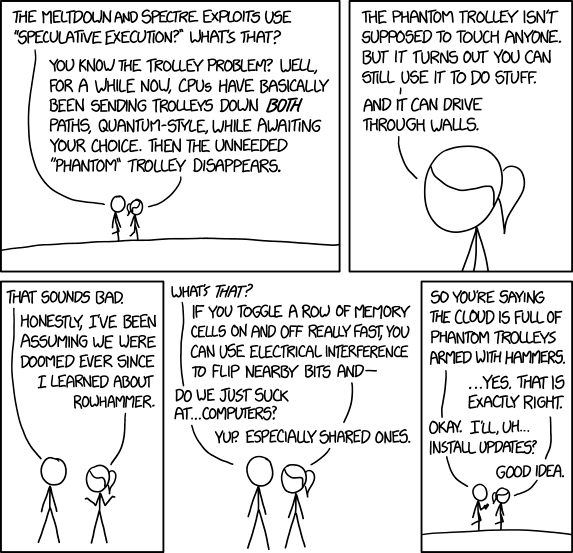
+\begin{block}{Meltdown and Spectre exploits\cite{xkcd}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[height=0.7\textheight]{meltdown_and_spectre.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Exploits}
|
|
|
+
|
|
|
+Exploits can be mitigated by:
|
|
|
+\begin{itemize}
|
|
|
+ \item Keeping OS, software and firmware up-to-date with latest patches.
|
|
|
+ \item Following best practices for software development.
|
|
|
+ \item Handling user input with caution.
|
|
|
+ \item Use past experience as a guiding light.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Backdoors}
|
|
|
+
|
|
|
+A backdoor is a hidden path left by the creators of a computer system that allows complete access to it by bypassing the normal authentication mechanisms used to limit access control.
|
|
|
+
|
|
|
+Some notable newest backdoors are:
|
|
|
+{\scriptsize \begin{itemize}
|
|
|
+ \item Samsung Galaxy devices running proprietary Android versions come with a back door\cite{replicant} that provides remote access to the data stored on the device.
|
|
|
+ \item Siri, Alexa, and all the other voice-control systems can be hijacked by programs that play commands in ultrasound\cite{vincent_2017} that humans can't hear.
|
|
|
+ \item Many appliances (like webcams) are sold with spyware sending lots of data to China.
|
|
|
+ \item All Verizon Wireless Android phones now come with app that allows OEMs backdoor access to install other apps without permission\cite{reddit}.
|
|
|
+ \item OnePlus found to be collecting personally identifiable analytics data\cite{android_police_2017} from phone owners.
|
|
|
+ \item Intel AMT backdoor allows hackers to gain control of PCs in under a minute\cite{verma_2018}.
|
|
|
+\end{itemize}}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Backdoors}
|
|
|
+
|
|
|
+Backdoors can be mitigated by:
|
|
|
+\begin{itemize}
|
|
|
+ \item Only buying products that respect privacy.
|
|
|
+ \item Avoiding unbranded electronics.
|
|
|
+ \item Using Free and Open Source Software (FOSS) and Hardware (FOSH) as much as possible.
|
|
|
+ \item Raising voices against (esp. Chinese and US) manufacturers that indulge in illegal and unethical practices.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{End-user awareness}
|
|
|
+
|
|
|
+``A computer is only as smart as the person using it.''
|
|
|
+
|
|
|
+{\scriptsize \begin{itemize}
|
|
|
+ \item One must have basic awareness about the computer system we use.
|
|
|
+ \item Always observe the system for any anomalies, like slowness, freezing, creation of unknown files, unknown app installations and similar unexpected behaviour.
|
|
|
+ \item Never install apps from unknown sources and do not accept toolbars or other adware bundled in installers.
|
|
|
+ \item Never install apps without looking at the permissions being requested.
|
|
|
+ \item Never click on scammy ads that require you to install something on the internet.
|
|
|
+ \item Always update your OS and apps.
|
|
|
+ \item Remember to back up your computer at regular intervals. Backups are the best solution to system software attacks.
|
|
|
+ \item If you do not plan to use your computer for a long time, it is better to keep it powered off.
|
|
|
+ \item Last but not the least, always prefer to use free and open source software because they can be easily audited for security issues.
|
|
|
+\end{itemize}}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\section{Network Security}
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Attacks using the Network Stack}
|
|
|
+
|
|
|
+Various attacks are possible using the network stack, especially using network layer (IP), transport layer (TCP/UDP) and application layer (HTTP/DNS/NTP) in conjunction. Some newest trending attacks are:
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Reflection and amplification attacks aided with application layer protocols like DNS and NTP.
|
|
|
+ \item Man-in-the-middle attacks.
|
|
|
+ \item Censorship (as in China, Iran and Cuba).
|
|
|
+ \item Cyber-espionage (as done by NSA and various companies).
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
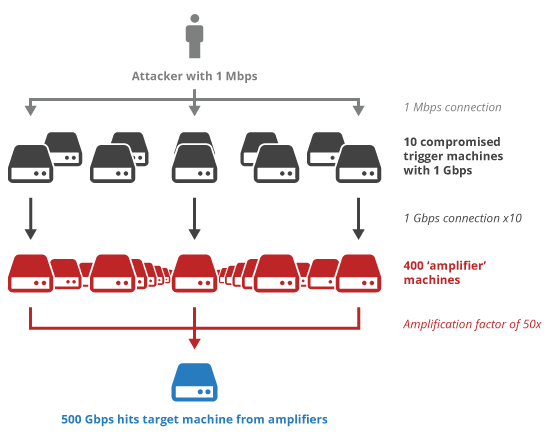
+\frametitle{Reflection and amplification attacks}
|
|
|
+
|
|
|
+{\scriptsize A reflection attack is a type of Distributed Denial of Service (DDoS) attack uses openly accessible servers of the aiding protocol (i.e. DNS or NTP) to attack a target from multiple locations. The attacker sends a request to these open servers spoofing or pretending to be the target. All the servers then send the response to the target at the same time, bringing it down.
|
|
|
+
|
|
|
+An amplification attack is a type of Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in the aiding protocol (i.e. DNS or NTP) servers to turn initially small queries into much larger payloads, which are used to bring down the victim’s servers.
|
|
|
+
|
|
|
+Reflection and amplification combined can generate attacks with a huge size and volume, often exceeding 300 Gbps.}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Reflection and amplification attacks}
|
|
|
+
|
|
|
+\begin{block}{Reflection attack\cite{ispcol}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[height=0.7\textheight]{reflection-attack.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Reflection and amplification attacks}
|
|
|
+
|
|
|
+\begin{block}{Amplification attack\cite{khandelwal_2014}}
|
|
|
+ \centering
|
|
|
+ \includegraphics[height=0.7\textheight]{amplification-attack.png}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Reflection and amplification attacks}
|
|
|
+
|
|
|
+Reflection and amplification attacks can be reduced by configuring open servers/resolvers in the following manner:
|
|
|
+\begin{itemize}
|
|
|
+ \item Disabling recursive/open access if not needed.
|
|
|
+ \item Limiting the number of services offered.
|
|
|
+ \item Limiting the people or resources that can access.
|
|
|
+ \item Employing rate limits on queries.
|
|
|
+ \item Filtering or not responding to unnecessary or anomalous requests.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Man-in-the-middle attacks}
|
|
|
+
|
|
|
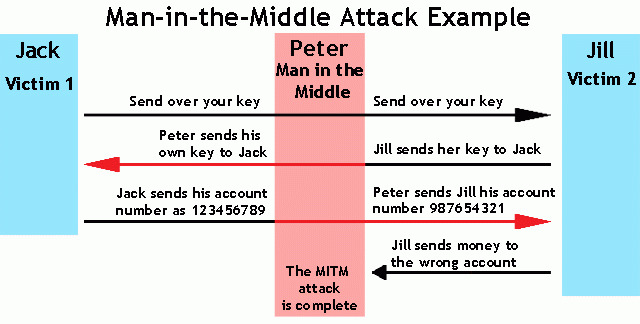
+A man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Man-in-the-middle attacks}
|
|
|
+
|
|
|
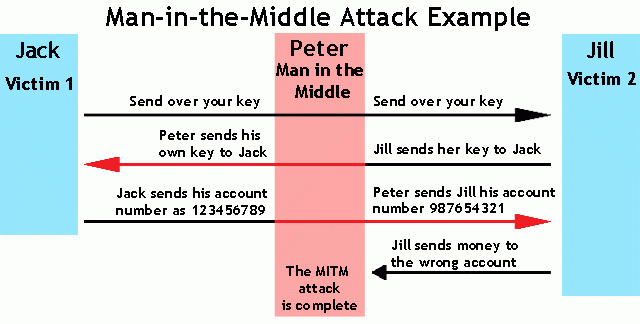
+\begin{block}{How is an MITM attack\cite{veracode_2017} performed?}
|
|
|
+ \centering
|
|
|
+ \includegraphics[width=\textwidth]{mitm.jpg}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Man-in-the-middle attacks}
|
|
|
+
|
|
|
+The chances of MITM attack can be reduced by:
|
|
|
+\begin{itemize}
|
|
|
+ \item Verifying the hostname or address in the address bar while connecting to a website or service.
|
|
|
+ \item Using TLS (SSL) everywhere and as much as possible.
|
|
|
+ \item Ensuring that your computer's OS supports DNSSEC.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Censorship}
|
|
|
+
|
|
|
+Internet censorship is the control or suppression of what can be accessed, published, or viewed on the Internet enacted by regulators, or on their own initiative.
|
|
|
+
|
|
|
+Censorship
|
|
|
+\begin{itemize}
|
|
|
+ \item restricts free and fair access to the Internet and creates inequality.
|
|
|
+ \item violates right to life by restricting access to emergency/help in oppressive regions.
|
|
|
+ \item violates right to free speech.
|
|
|
+ \item violates right to information.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Censorship}
|
|
|
+
|
|
|
+Internet censorship is practiced extensively in oppressive regions such as China, Cuba and Iran in order to
|
|
|
+\begin{itemize}
|
|
|
+ \item avoid citizens from getting information about the horrible actions of their regimes.
|
|
|
+ \item to prevent citizens from dissent and organizing uprisings.
|
|
|
+ \item to prevent citizens from sending information about the regime abroad.
|
|
|
+ \item to prevent access to art and literature not approved of by the regime.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+Even liberal nations practice censorship in response to copyright strikes, reducing access to P2P or to prohibit activities forbidden by the law.
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Censorship}
|
|
|
+
|
|
|
+\textit{``The Net interprets censorship as damage and routes around it.''} -- John Gilmore, Electronic Frontier Foundation
|
|
|
+
|
|
|
+Censorship can be defeated with the following steps:
|
|
|
+\begin{itemize}
|
|
|
+ \item Setting up your phone or computer to use non-ISP DNS like Google DNS or OpenDNS.
|
|
|
+ \item Browsing in HTTPS and using TLS (SSL) everywhere.
|
|
|
+ \item Using censorship circumvention tools.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Censorship}
|
|
|
+
|
|
|
+\begin{block}{Censorship circumvention tools}
|
|
|
+ \begin{itemize}
|
|
|
+ \item VPNs like OpenConnect/AnyConnect, OpenSSH, OpenVPN and WireGuard can defeat censorship in Turkey and Iran.
|
|
|
+ \item ShadowSocks and ShadowSocksR socks proxy servers can defeat censorship in China.
|
|
|
+ \item Streisand is a wizard that can help set up the above mentioned tools in a few minutes.
|
|
|
+ \end{itemize}
|
|
|
+\end{block}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Cyber-espionage}
|
|
|
+
|
|
|
+Cyber espionage, is the act or practice of obtaining secrets and information without the permission and knowledge of the holder of the information from individuals, competitors, rivals, groups, governments and enemies for personal, economic, political or military advantage using methods on the Internet, networks or individual computers through the use of proxy servers, cracking techniques and malicious software including trojan horses and spyware.
|
|
|
+
|
|
|
+For example, the National Security Agency has been spying on billions of individuals around the world with the PRISM and Fairview.
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Cyber-espionage}
|
|
|
+
|
|
|
+Cyber-espionage can be avoided by:
|
|
|
+\begin{itemize}
|
|
|
+ \item Avoiding using Microsoft Windows and preferring to use a free-and-open-source OS like GNU/Linux distros or FreeBSD.
|
|
|
+ \item Using HTTPS and TLS (SSL) everywhere.
|
|
|
+ \item Avoiding products with known backdoors.
|
|
|
+ \item Switching to secure email services like Protomail and Tutanota.
|
|
|
+ \item Using VPNs in public wifi hotspots.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\section{Application Security}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Attacks on applications today}
|
|
|
+
|
|
|
+The most common attacks on applications today are:
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Malicious email: spam and phishing attacks
|
|
|
+ \item DNS poisoning
|
|
|
+ \item Browser based attacks
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Spam and phishing emails}
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Email spam, also known as junk email, is a type of electronic spam where unsolicited messages are sent by email.
|
|
|
+ \item Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and money), often for malicious reasons, by disguising as a trustworthy entity in an email.
|
|
|
+ \item Most spam and phishing emails are sent using botnets.
|
|
|
+ \item Since spam filters are heuristic-based, they cannot catch all possible spam and phishing email.
|
|
|
+ \item We need some way to validate the sender: DKIM and SPF.
|
|
|
+ \item We need a policy to handle spam: DMARC
|
|
|
+\end{itemize}
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
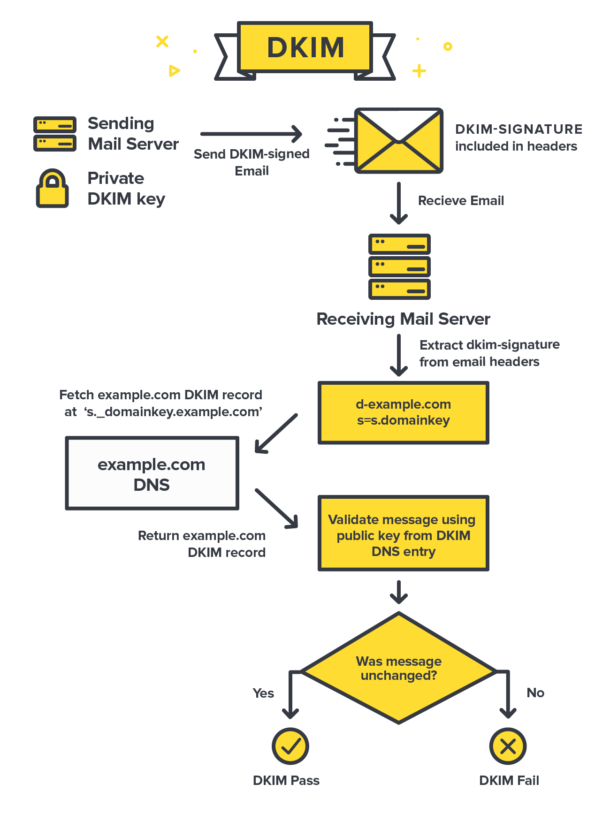
+\frametitle{DKIM \cite{postmark_dkim}}
|
|
|
+\centering
|
|
|
+\includegraphics[height=0.9\textheight]{DKIM.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
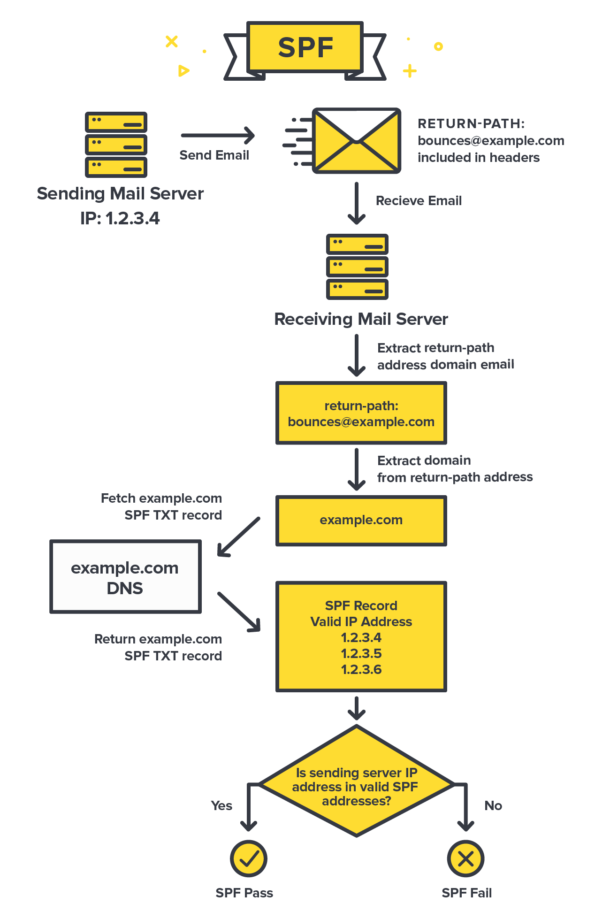
+\frametitle{SPF \cite{postmark_spf}}
|
|
|
+\centering
|
|
|
+\includegraphics[height=0.8\textheight]{SPF.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
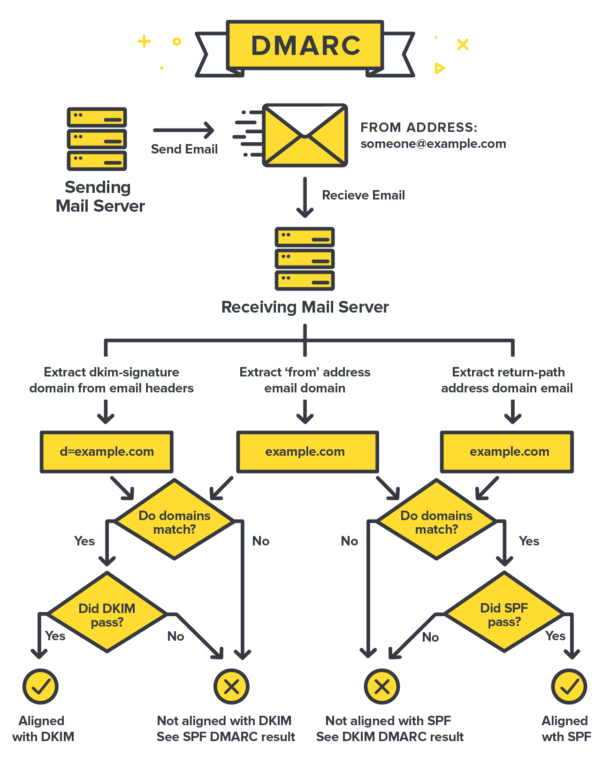
+\frametitle{DMARC \cite{postmark_dmarc}}
|
|
|
+\centering
|
|
|
+\includegraphics[height=0.8\textheight]{DMARC.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{DNS poisoning}
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver's cache, causing the name server to return an incorrect IP address. This results in traffic being diverted to the attacker's computer (or any other computer).
|
|
|
+ \item We need to figure out a way to ensure that the answer to the DNS query is valid: DNSSEC.
|
|
|
+ \item We need to ensure that the DNS communication between our computer and a resolver is safe and secure: DNSCrypt, DNS-over-TLS.
|
|
|
+
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
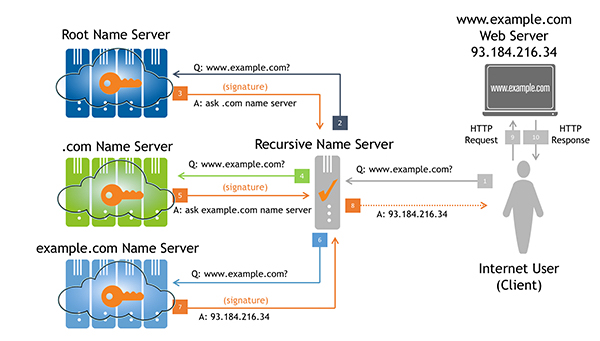
+\frametitle{DNSSEC \cite{verisign_blog_2017}}
|
|
|
+\centering
|
|
|
+\includegraphics[width=\textwidth]{DNSSEC.jpg}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
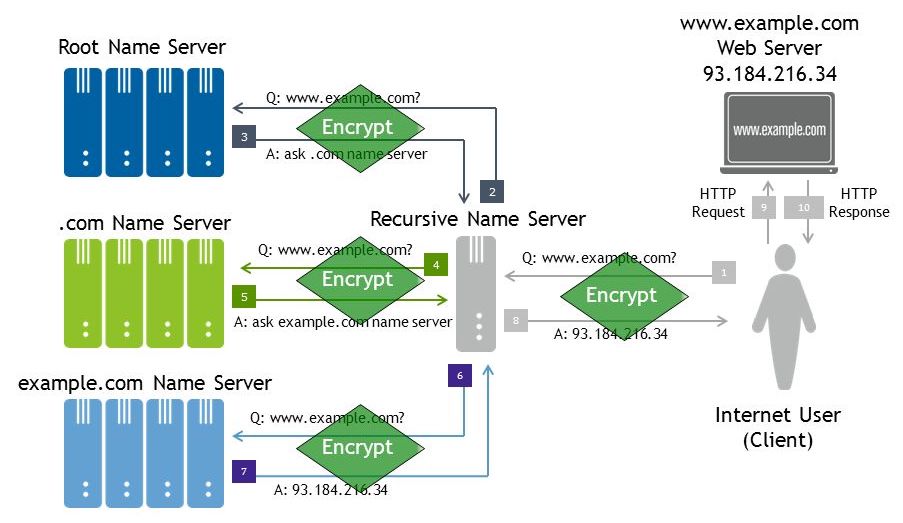
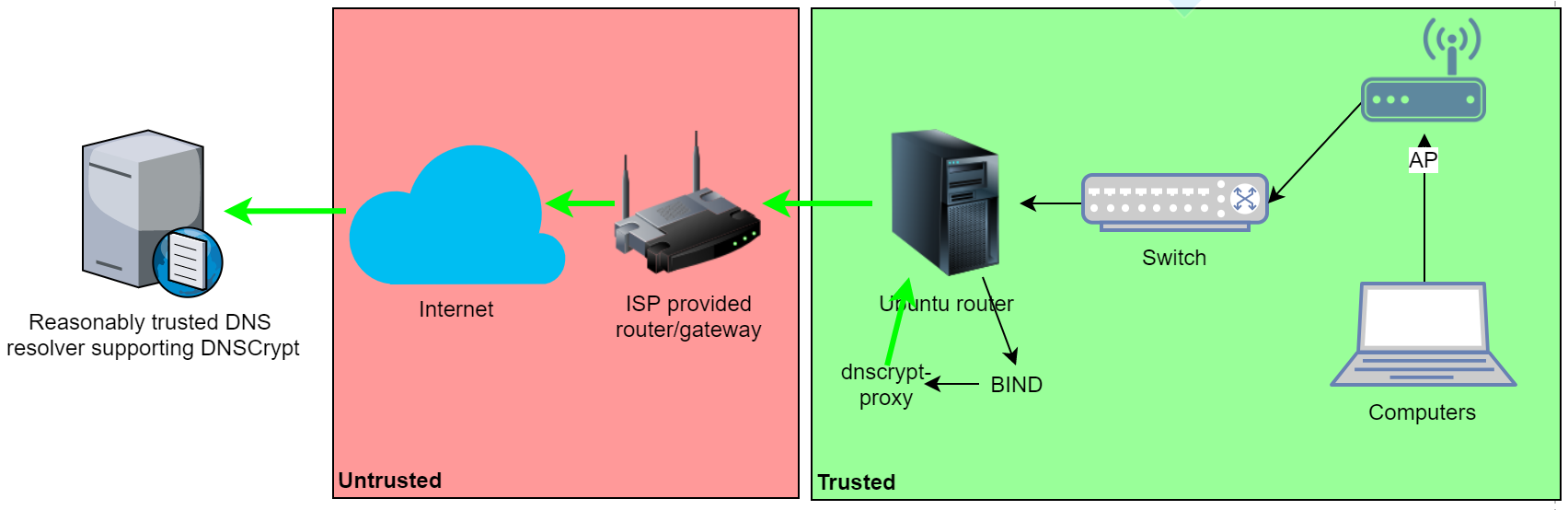
+\frametitle{DNSCrypt \cite{dan}}
|
|
|
+\centering
|
|
|
+\includegraphics[width=\textwidth]{dnscrypt.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{DNS-over-TLS \cite{slideplayer}}
|
|
|
+\centering
|
|
|
+\includegraphics[width=\textwidth]{dns-over-tls.jpg}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Browser attacks}
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Browsers can be exploited in numerous ways: cross-site scripting (XSS), Cross-Site Request Forgery (CSRF) and Clickjacking.
|
|
|
+ \item Many of these attacks can be mitigated simply by browsing over HTTPS instead of plain HTTP.
|
|
|
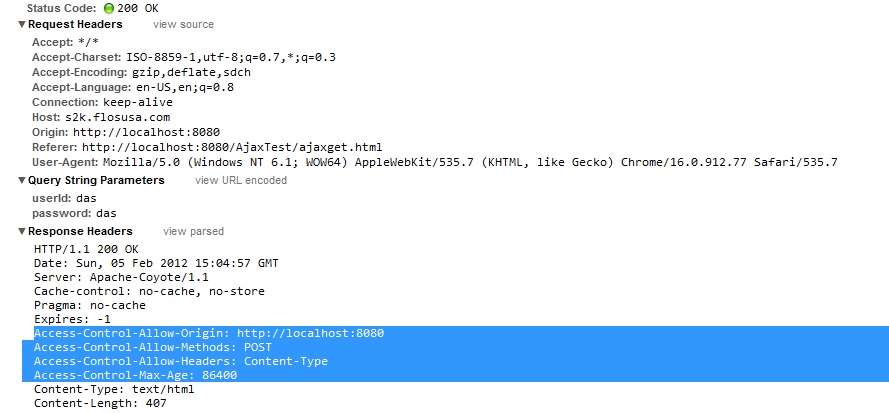
+ \item Many of the XSS and CSRF attacks can be mitigated by using the CORS and Access-Control-Allow-Headers headers.
|
|
|
+ \item HTTPS to HTTP downgrade attacks can be prevented by using the HSTS header.
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{Access-control-allow headers \cite{betterthanzero}}
|
|
|
+\centering
|
|
|
+\includegraphics[width=\textwidth]{access-control-allow.jpg}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
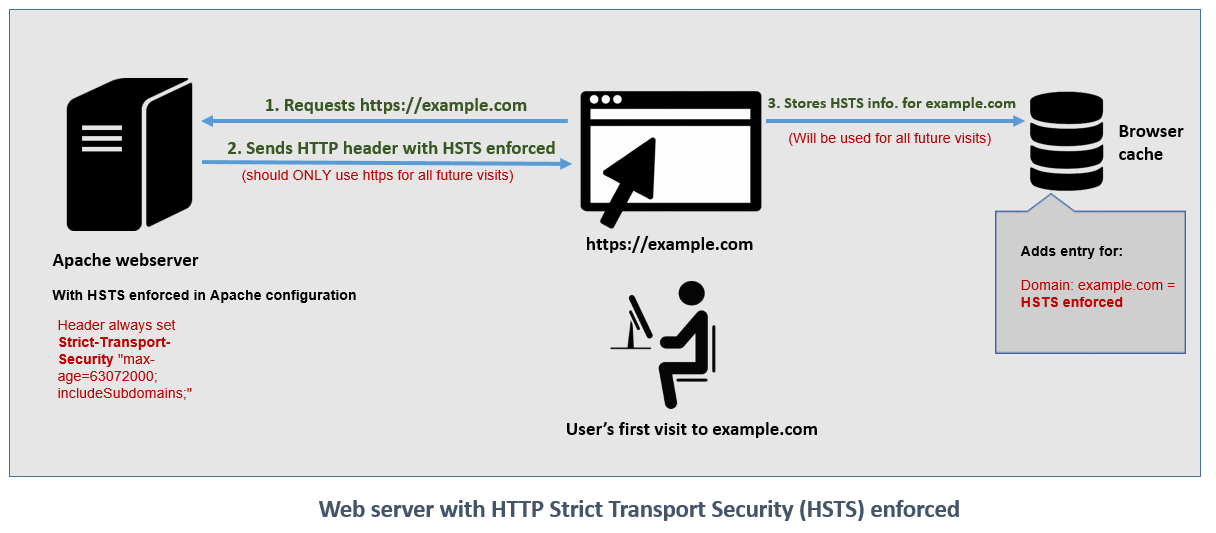
+\frametitle{HSTS header \cite{techglimpse}}
|
|
|
+\centering
|
|
|
+\includegraphics[width=\textwidth]{hsts.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\section{Transport Layer Security}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{TLS is no longer hard or expensive to implement}
|
|
|
+
|
|
|
+{\footnotesize \begin{itemize}
|
|
|
+ \item Contrary to popular belief, TLS (SSL) is not expensive anymore to implement.
|
|
|
+ \item The most CPU intensive part of TLS is the key exchange handshake that uses asymmetric-key RSA cryptography. It has long been replaced by lot less intensive ECC.
|
|
|
+ \item ECC is not only cheaper to implement, but also provides better security at low key sizes. E.g. 384-bit ECC is equivalent to 7680-bit RSA.
|
|
|
+ \item TLS connections now negotiate a one-time use session key using Elliptic-Curve Diffie-Hellman Ephemeral key exchange for forward secrecy in case the private key is compromised. Static RSA key exchange is no longer used.
|
|
|
+ \item Symmetric key encryption mechanisms now use AEAD like AES-GCM, AES-CCM and ChaCha20-Poly1305 which are faster and face less pipeline blocks compared to CBC ciphers.
|
|
|
+ \item The other cost associated with TLS, i.e., acquiring SSL certificates, is now gone. Let's Encrypt issues TLS certificates free of cost.
|
|
|
+\end{itemize}}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{TLS 1.3}
|
|
|
+
|
|
|
+The upcoming version of TLS, i.e., TLS 1.3 brings about massive overhauls to the protocol.
|
|
|
+
|
|
|
+Features removed\cite{valsorda_2017}:
|
|
|
+\begin{itemize}
|
|
|
+ \item Static RSA handshake
|
|
|
+ \item CBC MAC-then-Encrypt (MtE) modes
|
|
|
+ \item RC4
|
|
|
+ \item SHA1, MD5
|
|
|
+ \item Compression
|
|
|
+ \item Renegotiation
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
+\frametitle{TLS 1.3}
|
|
|
+Features improved\cite{valsorda_2017}:
|
|
|
+
|
|
|
+\begin{itemize}
|
|
|
+ \item Fixed DHE groups
|
|
|
+ \item RSA-Probabilistic Signature Scheme (RSASSA-PSS)
|
|
|
+ \item AEAD Nonce
|
|
|
+ \item Session IDs and Tickets
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+Features added\cite{valsorda_2017}:
|
|
|
+\begin{itemize}
|
|
|
+ \item Full handshake signature
|
|
|
+ \item Downgrade protection
|
|
|
+ \item Abbreviated resumption with optional (EC)DHE
|
|
|
+ \item Elliptic Curve 25519 and 448
|
|
|
+\end{itemize}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
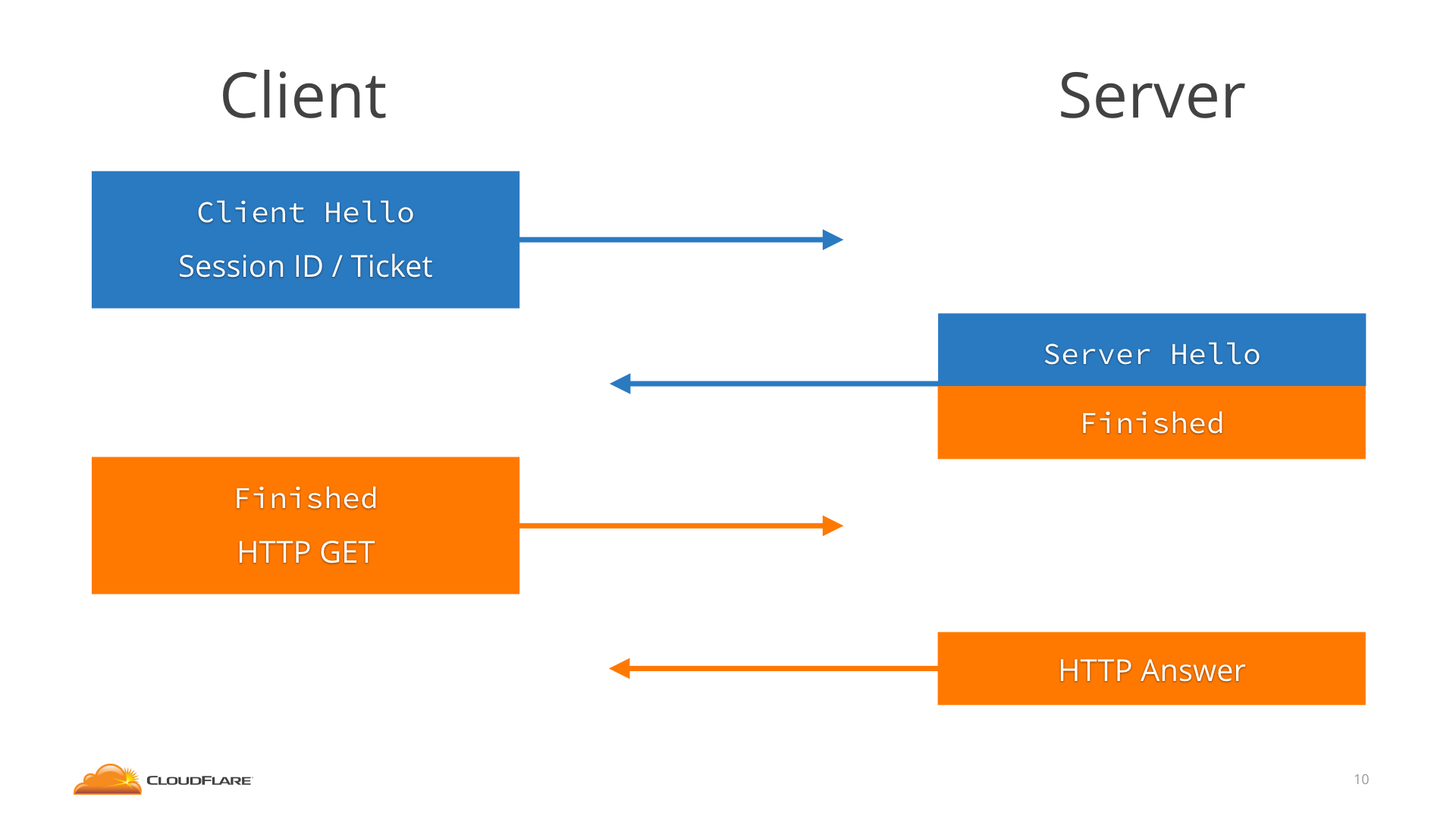
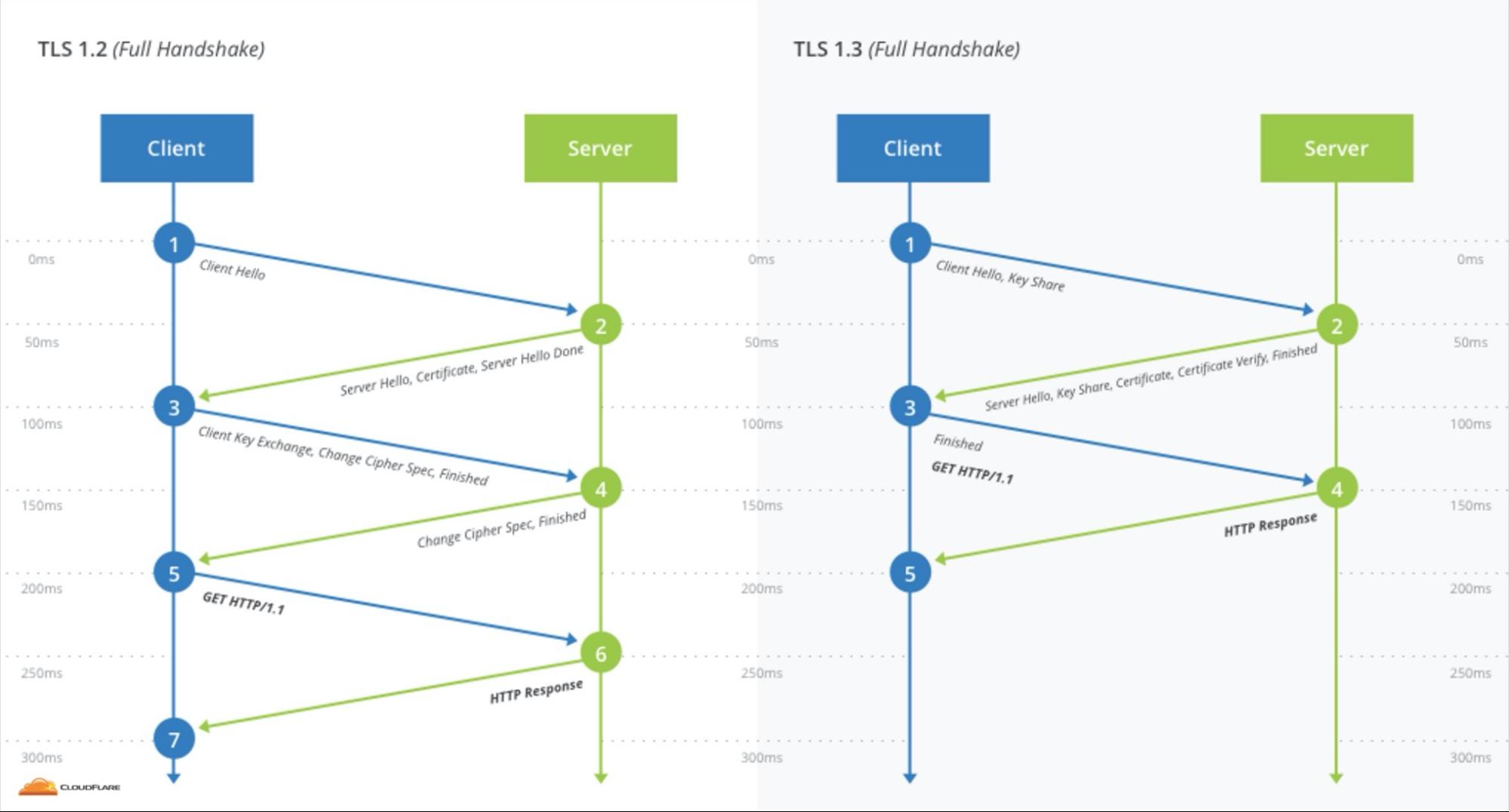
+\frametitle{TLS 1.2 2-RTT vs TLS 1.3 1-RTT handshake \cite{sullivan_2017}}
|
|
|
+
|
|
|
+\includegraphics[width=\textwidth]{tls13-handshake.jpg}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\begin{frame}
|
|
|
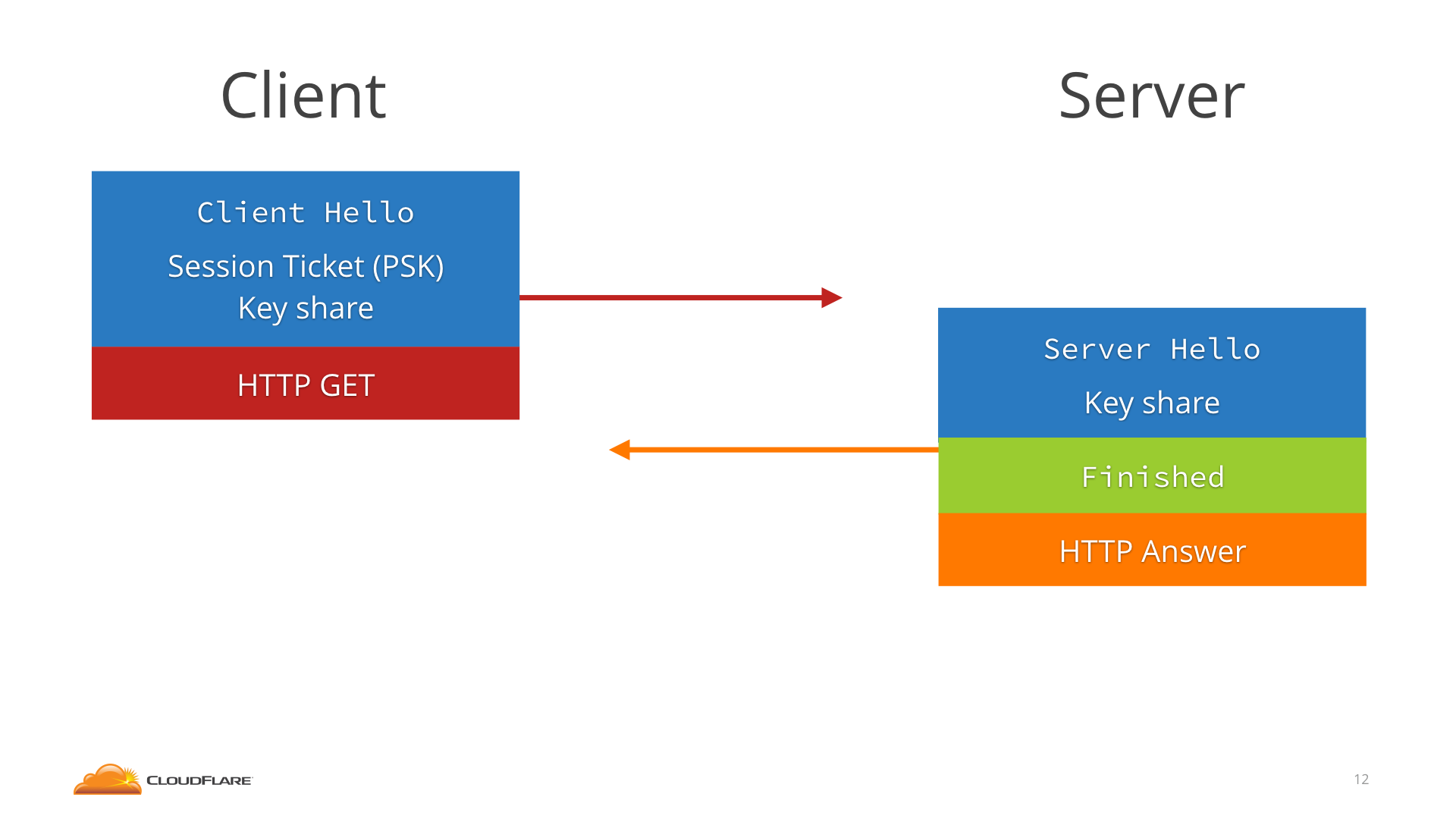
+\frametitle{TLS 1.2 1-RTT vs TLS 1.3 0-RTT session resumption \cite{valsorda_2017}}
|
|
|
+\centering
|
|
|
+TLS 1.2 resumption \hfill TLS 1.3 resumption\\
|
|
|
+\includegraphics[width=0.45\textwidth]{tls12-resumption.png}
|
|
|
+\includegraphics[width=0.45\textwidth]{tls13-resumption.png}
|
|
|
+
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\section{References}
|
|
|
+\begin{frame}[allowframebreaks]
|
|
|
+ \frametitle{References}
|
|
|
+ \scriptsize{\bibliographystyle{IEEEtran}}
|
|
|
+ \bibliography{references}
|
|
|
+\end{frame}
|
|
|
+
|
|
|
+\setbeamercolor{background canvas}{bg=matblue}
|
|
|
+\setbeamercolor{normal text}{fg=white}
|
|
|
+\begin{frame}[plain, b]
|
|
|
+\centering
|
|
|
+\huge \textcolor{white}{Thank You}
|
|
|
+\normalsize
|
|
|
+
|
|
|
+\vspace*{\fill}
|
|
|
+
|
|
|
+ \begin{beamercolorbox}[wd=\paperwidth]{section in head/foot}
|
|
|
+ \centering
|
|
|
+
|
|
|
+\vskip10pt
|
|
|
+\end{beamercolorbox}
|
|
|
+ \end{frame}
|
|
|
+
|
|
|
+\end{document}
|